It is a fact that today’s modern warfare has changed and shifted.
Cybersecurity plays an increasingly important role, we are exposed to some sophisticated attacks from unexpected malware, forcing us to act fast and change defence methodology.
This process divided into two main steps:
- Identifying most valuable assets which are usually one’s sensitive data and IP.
- Increasing control over the sensitive data and improving intelligence.
These steps will assist in buying time until a reaction and respond to an attack will take place. In today’s world enterprise data landscape compels to this process as data changes, formats and file types varies on a daily basis, where enormous volumes of data is generated by the minute, says Yaniv Avidan, CEO and co-founder MinerEye.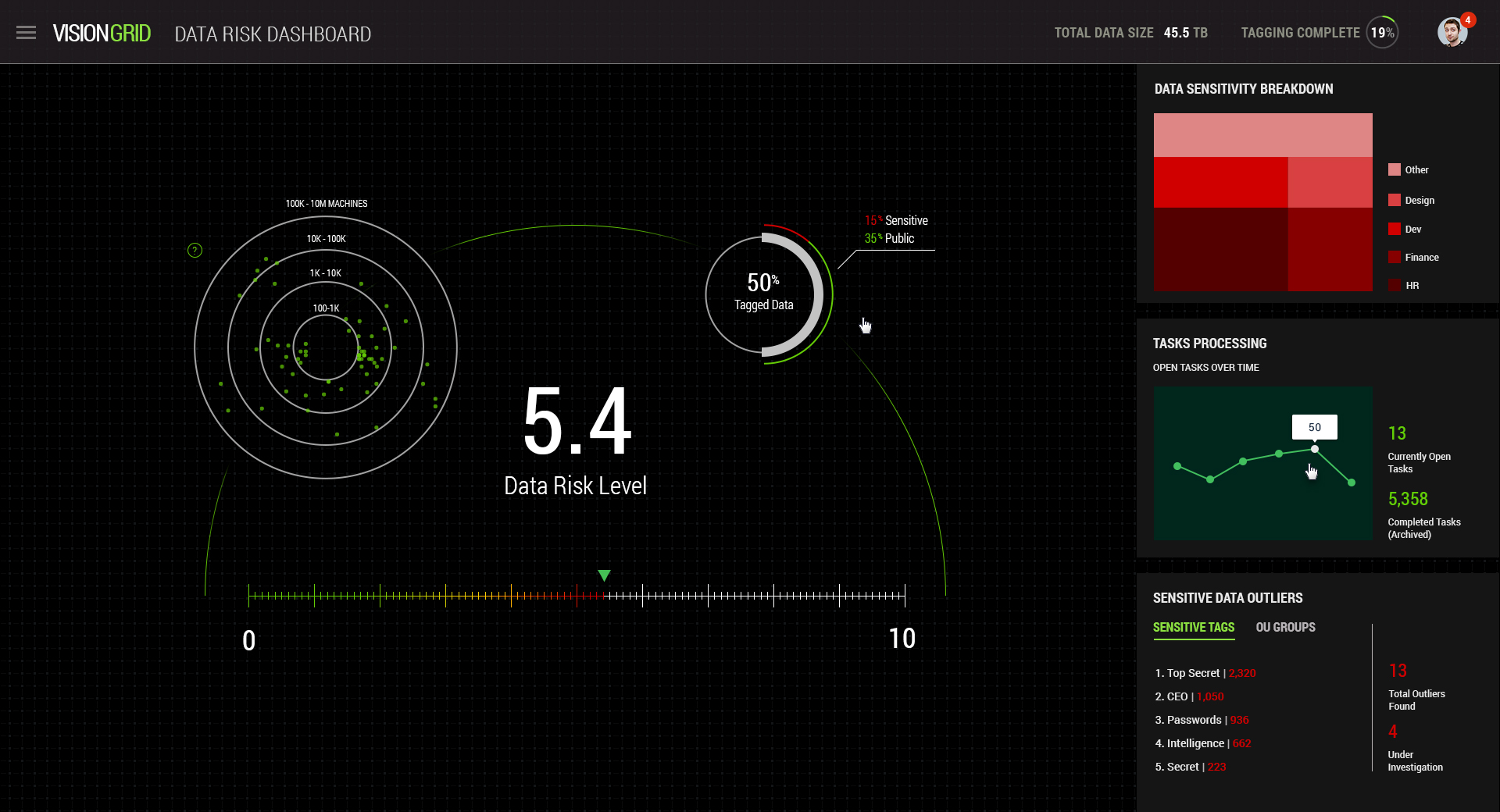
Data protection is a field that requires enormous efforts and resources. MinerEye has developed a unique technology that minimises these efforts to nearly zero by automating critical activities. Every C level executive in a company can tell between public information and a piece of data he would like to control; business models, processes, unique intellectual property, trade secrets, customers and employees private and protected info etc.
The challenge MinerEye has managed to solve is the knowhow in categorising, classifying and mapping the data in order to help an organisation to define and determine better data protection strategy. We developed a unique technology that can point the similarity among two data files without extracting the content. This process is done for enormous data volumes (up to one terabyte) within few hours.
MinerEye provides automated identified and categorised data divided into clusters of similar documents and files, while filtering out those cluster files that do not match the file patterns. Our platform supports the essential part in data protection, an ongoing continuous identification and classification of sensitive data. By visualising sensitive data clusters and their attributes, the system GUI enables users to tag the data and build private classification convention while, the backend, focuses on scanning, mapping and matching collected data to clusters, while the machine learns on the knowhow of a specific data behaviour.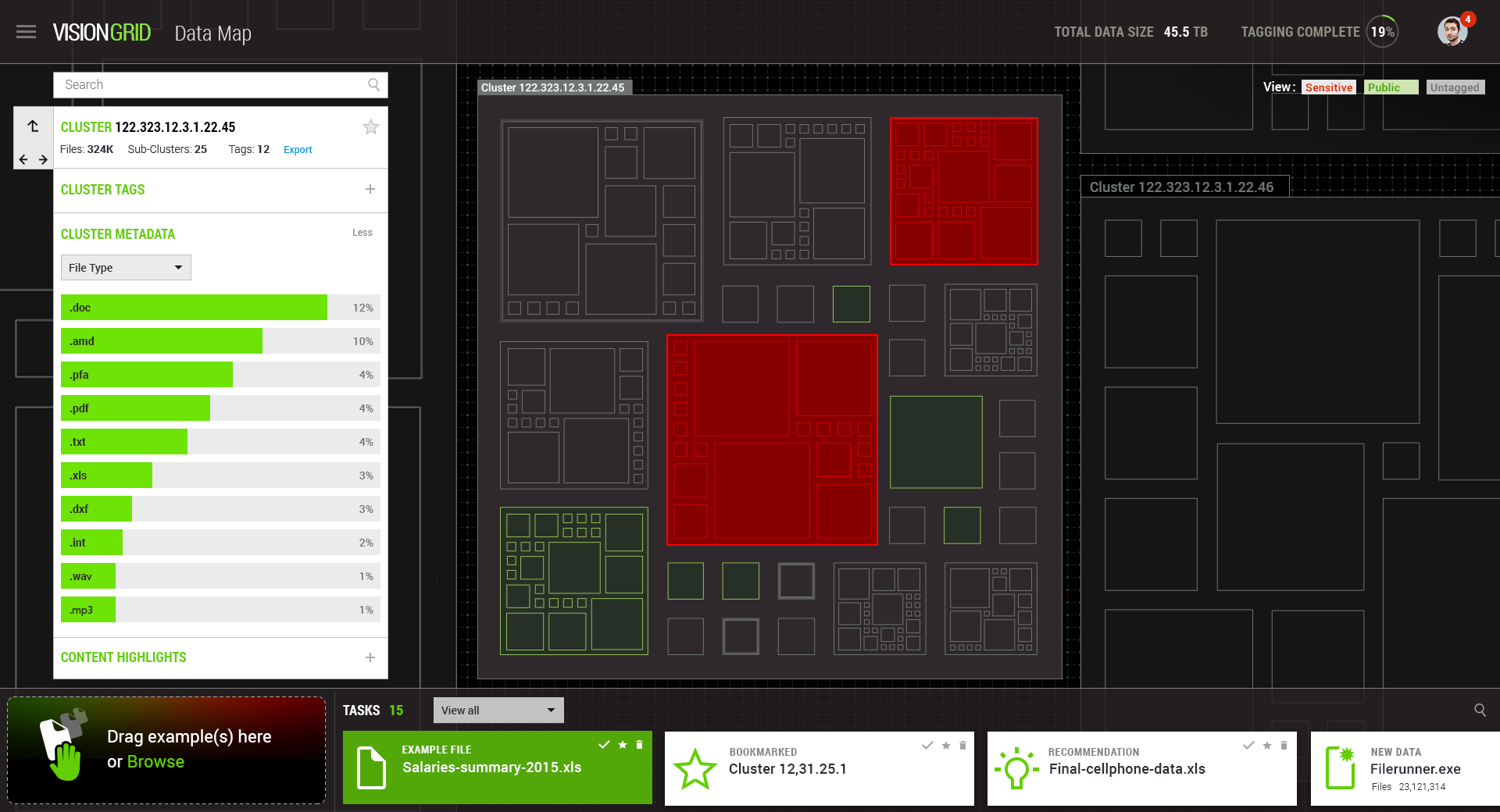
VisionGrid™ provides a pre-emptive valuable intelligence for sensitive data which forces Data Protection systems to act. MinerEye has shifted paradigms and concepts in classic machine learning by enforcing technology fusion of pattern recognition and computer vision. The technology gives a new definition to the word learning when a machine can infer correlation between two pieces of data, based on numerous examples. If there are no examples to learn from, the technology has the capability in building its own world of definitions by automatically categorising the data.
The author of this blog is Yaniv Avidan, CEO and co-founder at MinerEye.
About the Author:
Yaniv Avidan has more than 15 years of experience in the data analytics domain. He led several business units and corporate innovation teams in business intelligence, machine learning, big data and cyber security analytics. Previously he led teams of data scientists and cyber threat analysts at Intel in a corporate scale program and managed an advanced battle field simulation program for the IDF partnering with Lockheed Martin and Cubic Defense Systems. Yaniv holds a B.Sc. in Information Systems Engineering from the Ben-Gurion University in Israel.
Comment on this article below or via Twitter: @ VanillaPlus OR @jcvplus






