The latest 2015 Verizon Data Breach Investigations Report indicates that insider threats continue to be a top security concern. As employees go rogue, one effective insider threat prevention technology that has been instrumental for IT security is User Behaviour Analytics (UBA).
If you currently use a security identity event management (SIEM) tool to monitor user activity for threat management, and regulatory compliance, awesome! You have a head start, says Cindy Ng of Varonis. SIEM is an excellent starting point for security analytics, as it monitors system events captured in firewalls, OS logs, syslog, network traffic logs, and more.
If you have SIEM, you might wonder why you need UBA. At first glance UBA and SIEM appear to be very similar, however, upon closer inspection, they do different things.
By focusing less on system events, and more on specific user activities, UBA builds a profile of an employee based on their usage patterns, and sends out an alert if it sees abnormal user behavior. Typically UBA alerts can be sent via e-email, SMS, or even be piped into your SIEM.
Let’s go through the difference between SIEM and UBA to understand when to implement them.
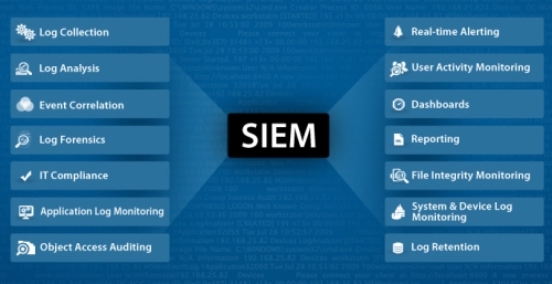
What is SIEM?
SIEM combines all security events from SIM (security information management) and SEM (security event management) functions into one central database, yielding important security analysis, reports, and alerts in one centralised place.
And how does SIEM work?
SIEM systems store, analyse, and correlate a multitude of security information, authentication events, anti-virus events, audit events, intrusion events, etc. Any anomalous event captured in a rule alerts a security officer/analyst to take swift action. Plus, SIEM tools can also help compliance managers meet strict regulatory requirements.
Do they collect data themselves?
SIEM systems aggregate logs, most commonly through reading event viewer data, receiving standard feeds from SNMP traps, or Syslog, or sometimes with the help of agents. These feeds come from user devices, network switches, servers, firewalls, anti-virus software, intrusion detection/prevention systems, and many more. Once all of the data is centralised, it runs reports, “listens” for anomalous events, and sends alerts.
SIEM Rules and Alerts
For the SIEM tool to identify anomalous events, and send alerts, it’s important that an administrator create a profile of the system under normal event conditions. SIEM alerts can be pre-configured with canned rules, or you can custom create your own rules that reflect your security policies.
After events are sent to the system, they pass through a series of rules, which will generate alerts. Alerts indicate that a series of events has happened and needs attention. Keep in mind, with potentially thousands of devices, and different sources to monitor, each generating a couple thousand records or more a day, there will be plenty of information to sift through. So, use SIEM rules to reduce the number of events down to a small number of actionable alerts that signal actual vulnerabilities, threats, or risk.
Profile of a SIEM Buyer
Bottom line: Security officers/analysts who want a high-level overview of all their devices, platforms, network, and their events generated will want to take a closer look at SIEM tools.
Quick! Tell me what UBA is so I can figure out how it’s different from SIEM.
UBA solutions are defined by their ability to audit, and analyse an individual’s file and application access, then connect these disparate points to flag that individual as engaged in suspicious behaviour.
How does UBA work?
Not all UBA software is the same. The market is composed of business intelligence, database, security, and fraud detection, as well as vendors that specialise in insider threats. (To learn more about the differences, you can read this post from Varonis’ technical specialist, Andy Green What is UBA?)
Regardless, UBA helps mitigate the risks of both insider threats, and external attackers by using the same principle. First, a normal baseline is defined based on user behaviour – file access, logins, network activity, etc. – over an extended period. Second, UBA can quickly identify user deviations from that norm, and generate an alert. In the case of attackers entering the system, UBA can tell whether an employee’s credentials are being used by outsiders. For legitimate employees, UBA can also spot changes in activity that signal insider data theft, or IT sabotage.
Do they collect data themselves?
UBA processes a wide variety of sources usually without volume, variety, and velocity constraints. With files, emails, and other IT resources being accessed and created every second of every day, good UBA software has the ability – often with the assistance of agents, and collectors – to process this enormous load and report anomalies in, or near, real-time.
UBA Rules and Alerts
UBA software supports canned rules that allow an IT admin to configure a template to, say, spot accesses to a sensitive file during non-business hours. But UBA really excels at handling the unknown. In the background, the UBA engine can baseline each user’s normal activity, and then spot variances– in whatever form they reveal themselves. For example, it can automatically spot thousands of “file delete” actions in a short time windows, unusual directory visits, or launches of rarely used apps, all perhaps indicating that a user is behaving uncharacteristically.
Profile of an UBA Buyer
Bottom line: UBA software can effectively alert security officers when the baseline activity within an environment exhibits anomalies, signaling a potential attack.
If I have SIEM, would I need UBA?
Excellent question! Here are three recommendations:
- Determine if you want SIEM to analyse security event data produced by security devices, network infrastructures, systems, and applications. Or UBA to gain deep insight into what users on a system are doing — their activities and file access patterns.
- Use cases also really help security officers identify, clarify and prioritise requirements for deciding on which solutions to use. Plus, it’s a good way to really “get” the differences between these complementary technologies.
If you have any projects related to compliance, and need to track access activity, here are some relevant SIEM use cases:
- Compliance reporting
- Monitoring of events – access activity, data access, application activity, and event management
Concerned with insider threats, and protecting organisation digital assets? Below are relevant UBA use cases:
- Insider threat enterprise security
- Protecting organisations with high-value IP, or sensitive data that needs protection– such as financial, government, telecom, education, hospitals, retail, etc.

Cindy Ng, technical analyst, Varonis If you’re already deployed SIEM, evaluate its user monitoring, profiling, and anomaly detection capabilities to determine whether they can be adapted to satisfy your use cases before turning to UBA technology.
In short, both SIEM, and UBA have important use cases to help an organisation meet their business and security needs. Because insider attacks are real, and costly, don’t overlook UBA as it is an excellent complement to SIEM.
By Cindy Ng, technical analyst, Varonis