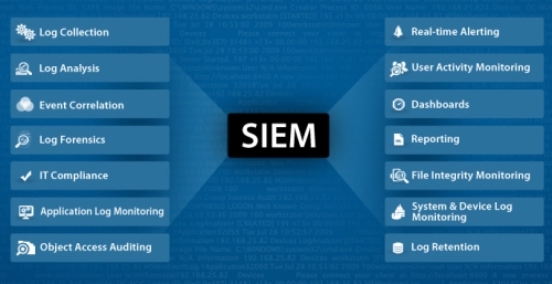
SIEM
AWS launches aggregation service for security alerts from disparate sources and runs continuous compliance checks
Amazon Web Services Inc., an Amazon.com company, has announced the general availability of AWS Security Hub, a service that gives customers a central place to manage security and compliance across an AWS
Read moreAlienVault expands USM anywhere to include endpoint detection and response capabilities
AlienVault, a provider of Unified Security Management (USM) and crowdsourced threat intelligence, has announced the general availability of Endpoint Detection and Response (EDR) capabilities in USM Anywhere.
Read moreFour ways to reinforce your SME against cyber threats
Despite its name, the small and medium-sized enterprise (SME) sector is colossal in terms of size and revenue, says Sneha Paul, product consultant at ManageEngine.
Read moreExpansion of network access control platforms sets the stage for accelerated revenue growth
Network access control (NAC) vendors recently made four significant technological improvements to make their platforms indispensable to network security. These enhancements include the offer of endpoint visibility, bidirectional integration with
Read moreBreaches are definitely costly, says Mandana Javaheri
When it comes to network forensics and security investigations, there are two main challenges that any public or private organisation will face. Breaches are definitely costly.
Read moreHow well protected are you in today’s cyber-threat landscape? – Part 2
The ‘cyber kill chain for intrusion detection’ is a wonderfully succinct concept that models intrusions in a network, from reconnaissance through to culminating in a system of attack. Hackers leave digital footprints
Read moreThe difference between SIEM and UBA
The latest 2015 Verizon Data Breach Investigations Report indicates that insider threats continue to be a top security concern. As employees go rogue, one effective insider threat prevention technology that
Read more