European IT security company Balabit announced the results of a survey on the top 10 most popular hacking methods.
The findings came from surveying people at Black Hat events in US and Europe and revealed that the insider threat is definitely the most dangerous. In most cases the hackers are reported to use social engineering techniques to gain network access.
The recent data breach of more than 10,000 US Departments of Justice and Homeland Security staff and over 20,000 supposed Federal Bureau of Investigation (FBI) employees is a reminder that becoming an insider by using social engineering tactics is much easier for hackers than writing zero-day exploits.

“The highest risk to corporations is when outside attackers gain insider access, as they can stay undetected within the network for months. Balabit aims to support organisations to know their enemy by knowing who is behind their user accounts, and determining whether it is a legitimate user or a masked hacker. This should be the fundamental priority in every kind of organisation’s IT security strategy,” said Zoltán Györkő, CEO at Balabit.
Over 70% of IT security experts consider insider threats more risky
54% of the survey respondents said that, according to their experience, organisations are still afraid of “hackers” breaking into their IT network through their firewall – but at the same time over 40% of them said that they already clearly see that first-line defence tools, such as firewalls are just not effective enough to keep the hackers away. Balabit surveyed whether IT security experts consider the outsider or insider threats more risky, when those attacks that are started from outside and primarily target insider’s privileged users accounts – so would never be successful without becoming an insider – belong to the insider category. In When a data breach occurs, the fact that it was a result of an accidental or intentional insider “help” is secondary. The survey results point to an efficient defence strategy: over 70% of those surveyed said that insiders are more risky.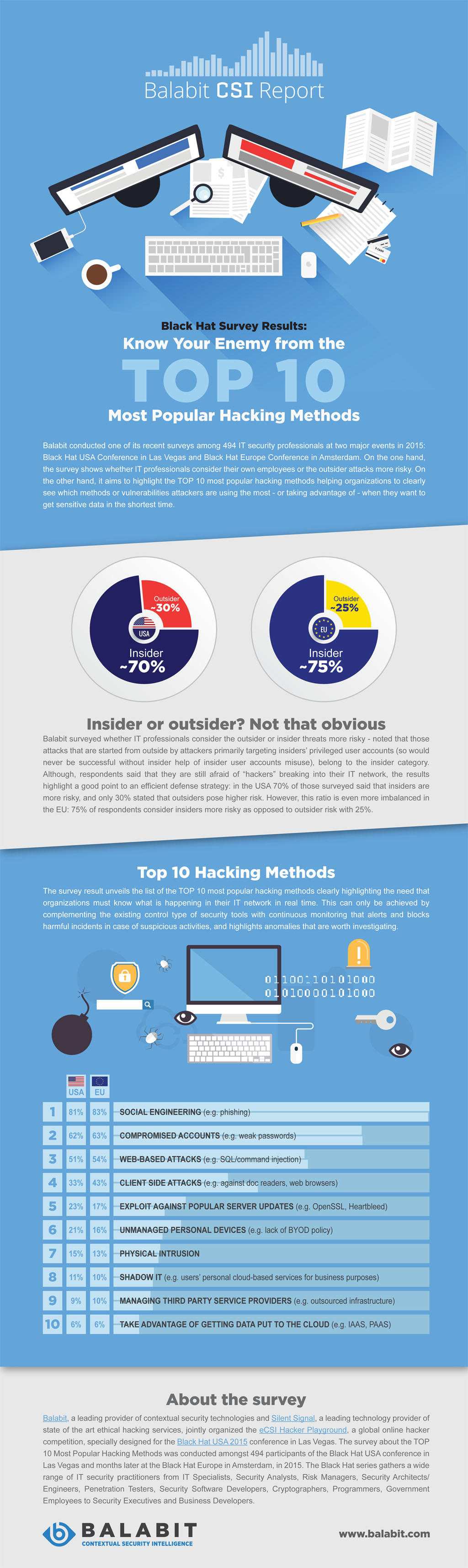
Comment on this article below or via Twitter: @ VanillaPlusMag OR @jcvplus