The telecoms market is an increasingly crowded one, with incumbents and challengers alike struggling to find new streams of revenue and contending with ever-smaller margins. Driving up profit now means improving revenues from existing areas, and focusing on reducing revenue leaks. Unfortunately, perhaps the most prevalent problem in the industry is also the one which has the potential to inflict the most damage: fraud.
The problem of fraud is not a new one, and despite innovations and developments in telecoms technology, the frequency of fraud attacks remains unaffected. The Communications Fraud Control Association estimates global telecoms fraud costs the industry €34.5 ($38) billion each year, with the most prevalent fraud being International Revenue Share Fraud, facilitated most frequently through PBX hacking and Wangiri, says Katia Gonzalez, head of Fraud Prevention Operations at BICS.
LTE roaming fraud attacks are also on the rise, due to the explosion in LTE roaming in recent years. This is driven by the availability of data and mobile broadband services across different regions and the demand from end-users to access high quality, next-generation services abroad. Incidents of LTE roaming fraud can take longer to identify than traditional and domestic attacks, and can cause huge revenue loss.
Fraud attacks on mobile operators not only cause significant damage financially, but also in terms of operators’ reputation, brand image and relationships with their customer base. As such, companies are often reluctant to share details of failings. Peers, stakeholders and customers will note any weaknesses and behave negatively in response.
The closed approach of many operators could be to the detriment of the industry, and instead the reverse strategy should be employed: cross-border collaboration. The cooperation and active sharing of information – of both attacks and suspicious activity – is of even greater importance given the rise of international LTE roaming fraud.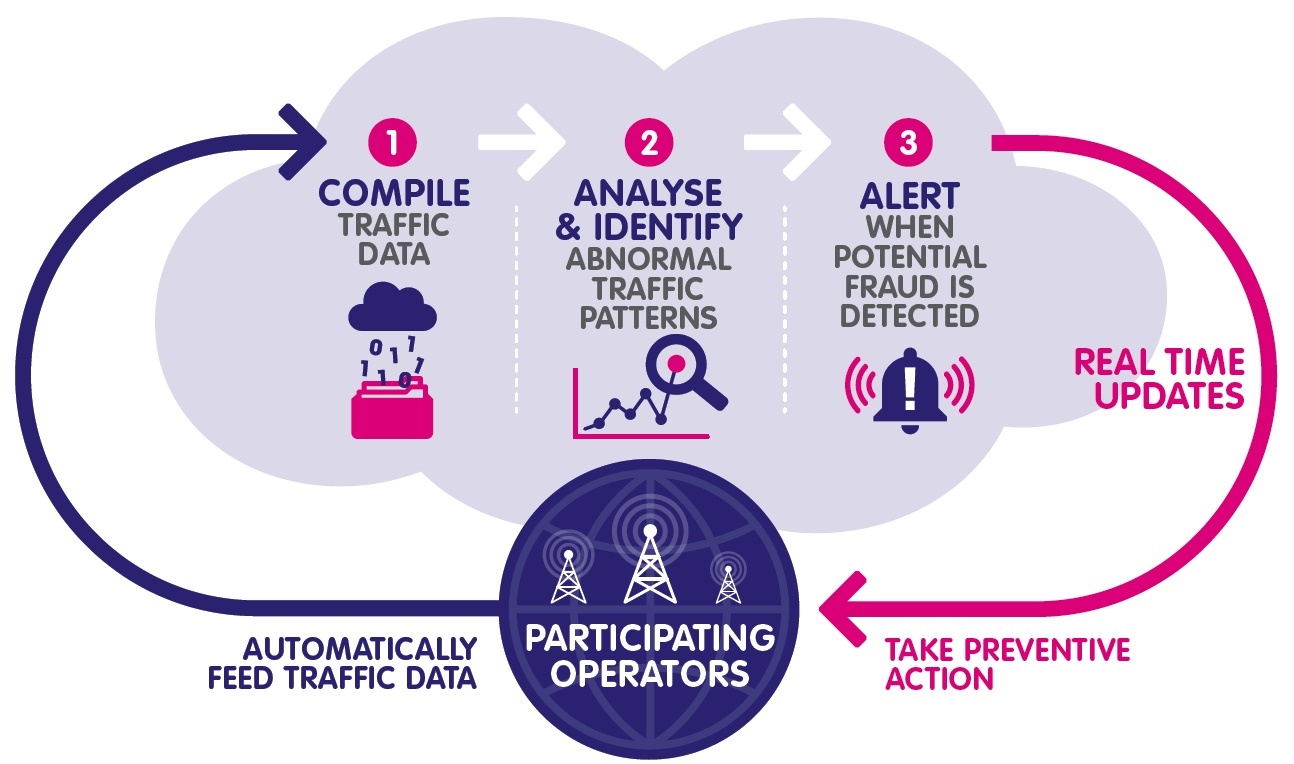
A major French operator, for example, reportedly saved around €130,000 ($141,811) in the first three months of this year due to this proactive approach. These savings were made possible through crowdsourcing information from operators worldwide on fraud attacks. This included incident profiling, originating numbers and geographical origin. All this intelligence can then be used to combat telecoms fraud, leading to action before the customer is aware of the attack, thus mitigating damage to a company’s reputation and its customer relations.
Wholesale carriers are perfectly positioned to analyse information from around the world and create actionable data from fraud attacks, both successful and attempted. Sharing this with and among operators allows these businesses to defend themselves against current threats, and pre-empt fraud trends that other operators are experiencing across the globe. As LTE roaming technologies develop, a cross-border collaborative strategy is the only viable way to create a safer, more cooperative industry.
Two examples of the types of fraud telecoms service providers can expect to face include:
1. International revenue share fraud: One of the most damaging and hard to prevent schemes. Various techniques are used to encourage large amounts of fraudulent international calls which are then routed to premium rate numbers or to countries with high termination fees, often through a number of international operators. By routing to the most expensive destinations, criminals have the opportunity to create large charges very quickly.
Some of the most common techniques to perpetrate international revenue share fraud are Wangiri attacks and PBX hacking.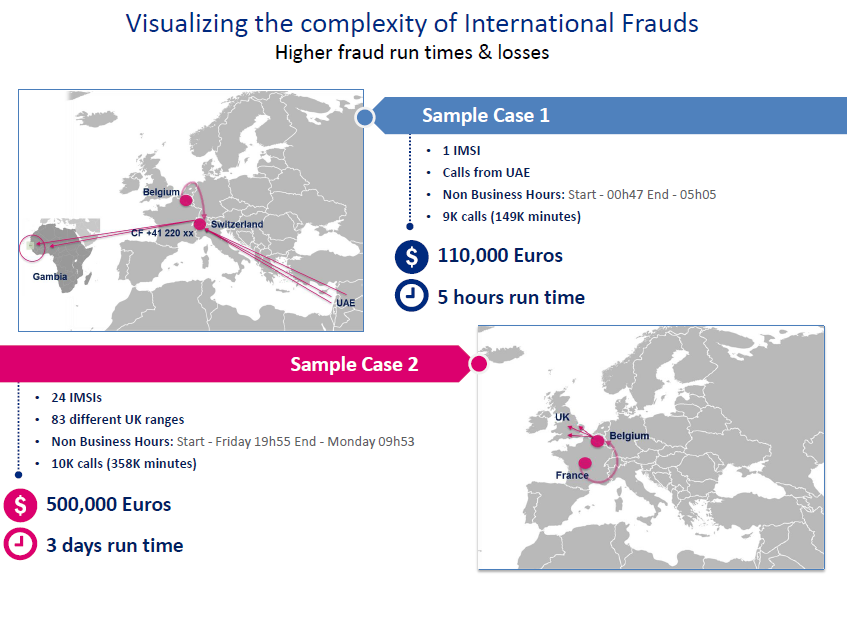
- Wangiri: A large number of calls are made at random and cut off after one ring in an attempt to get the recipient to return the call, which is then connected to a premium number. These short calls are often combined with SMS messages sent to users encouraging them to call the same premium numbers. This type of activity has expanded and now targets users from all SP types, from MVNO to OTT services, by sending urgent messages requesting a call-back to a premium rate number.
- PBX hacking: One of the oldest forms of telecoms service abuse which occurs when hackers target private branch exchanges and make a high volume of calls to premium rate or highly rated overseas numbers.
2. False answer supervision: Here, traffic is intercepted by a third party that claims the call lasts for longer than it actually does, has been established before it occurred, or has been answered when it has not. The charge is then made for the increased call time, or for calls which never took place, with a direct impact on the end users invoice.
The author of this blog is Katia Gonzalez, head of Fraud Prevention Operations at BICS.
Comment on this article below or via Twitter: @ VanillaPlus OR @jcvplus






